Georgia Tech uses SSL certificates issued by Incommon.org to secure communications between our web servers and clients. These instructions will walk through the process of generating a Certificate Signing Request (CSR), requesting a new certificate through incommon, and installation of the issued certificates on RHEL5/6/7 servers running apache 2.4.x
Configure SSL
BEFORE requesting a CSR, make sure you have SSL configured correctly on the server.
Generate a Server Key
If this is the first time a certificate is being installed on this server, you'll have to generate the private key from which subsequent certificates and signing requests will be derived. Use the following commands to generate a new private key:
cd /etc/pki/tls/privateopenssl genrsa -out <canonical-hostname>.cc.gatech.edu.key 4096
The output should look like this:
Generating RSA private key, 4096 bit long modulus ......................................++ ......................................................................++ e is 65537 (0x10001)
This should result in a server key like this:/etc/pki/tls/private/<canonical-hostname>.cc.gatech.edu.key
Note that the contents of this file should be considered secret and never saved or transmitted anywhere else. Removing or modifying this file will break all SSL/TLS transactions.
Generate a CSR (Certificate Signing Request)
As a convention, certificates should be named after the common name, so a certificate file for help.cc.gatech.edu would be named help.cc.gatech.edu.crt. Certificate files are not secret, and the permissions should be set so that at least the web server user has read access (644 is fine).
Here is the command to generate the CSR:
(note: in Ubuntu you will cd to /etc/ssl/certs/ instead of /etc/pki/tls/certs)
cd /etc/pki/tls/certsopenssl req -new -key ../private/<canonical-hostname>.cc.gatech.edu.key -out <canonical-hostname>.cc.gatech.edu.csr
When prompted to fill out some fields of the certificate, use these values:
USGeorgiaAtlantaGeorgia Institute of TechnologyCollege of Computing<canonical-hostname.cc.gatech.edu>certificates@cc.gatech.eduPlease use the settings above exactly, with the exception of the Common Name. The Common Name should be the hostname that will be used to access the service (i.e. if the server name is mud.cc.gatech.edu, but this certificate is an application at https://app.cc.gatech.edu, the Common Name would be app.cc.gatech.edu).
This should result in a text file like this:/etc/pki/tls/certs/<canonical-hostname>.cc.gatech.edu.csr
To read the contents of the CSR file:cat /etc/pki/tls/certs/<canonical-hostname>.cc.gatech.edu.csr
The contents look like this, only with more text between the dashed lines:
-----BEGIN CERTIFICATE REQUEST----- MIIB9DCCAV0CAQAwgbMxCzAJBgNVBAYTAlVTMRAwDgYDVQQIEwdHZW9yZ2lhMRAw [ ... TRUNCATED ...] -----END CERTIFICATE REQUEST-----
Enter the CSR into Incommon
Log into incommon.org using the blue InCommon Federated Login button. Select Georgia Institute of Technology from the dropdown (if it isn't already selected). Once you are logged in, you will see a list of certificates. Follow the steps below to continue.
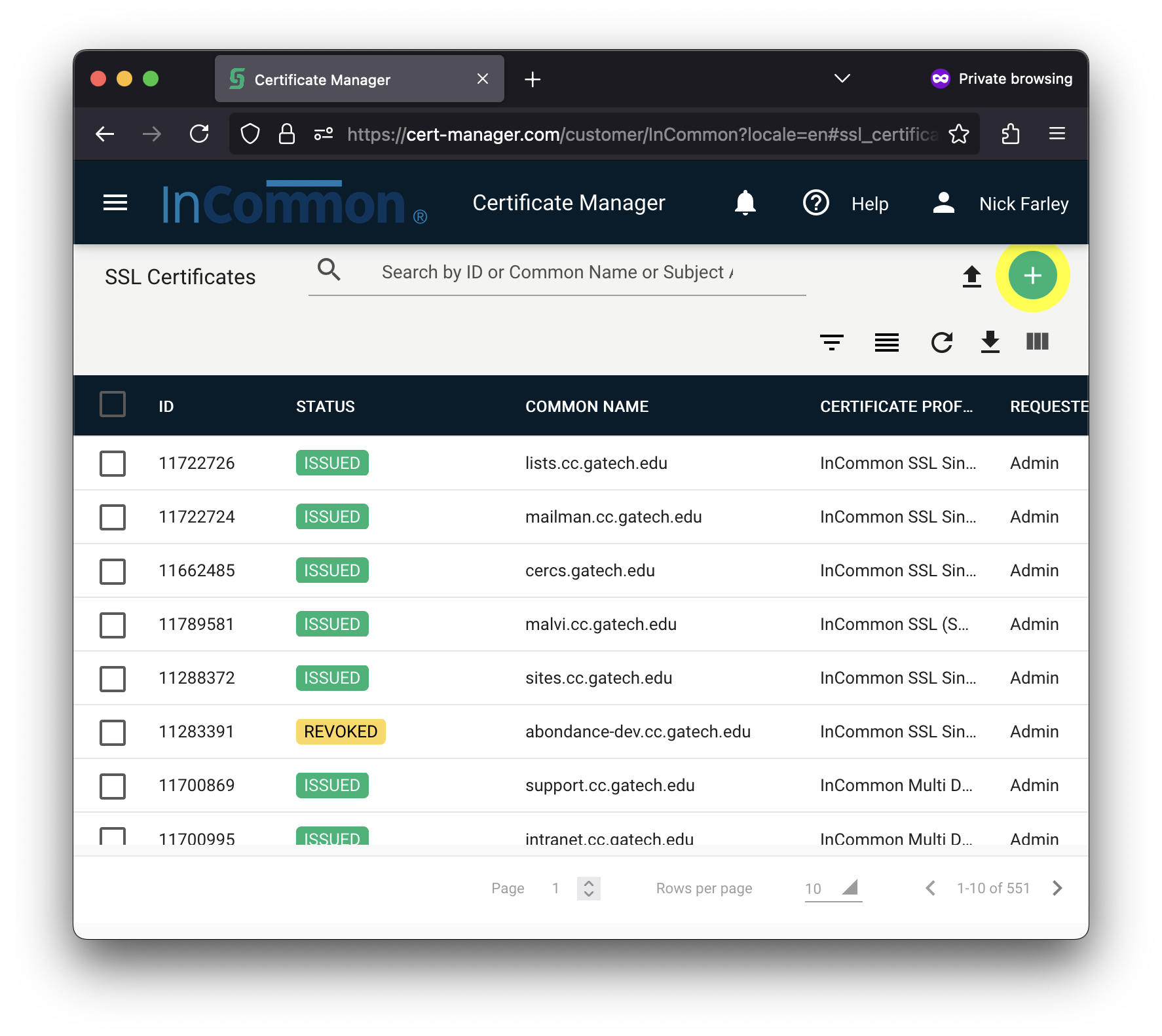 | To begin creating a new certificate, click the green plus icon, highlighted here in yellow. |
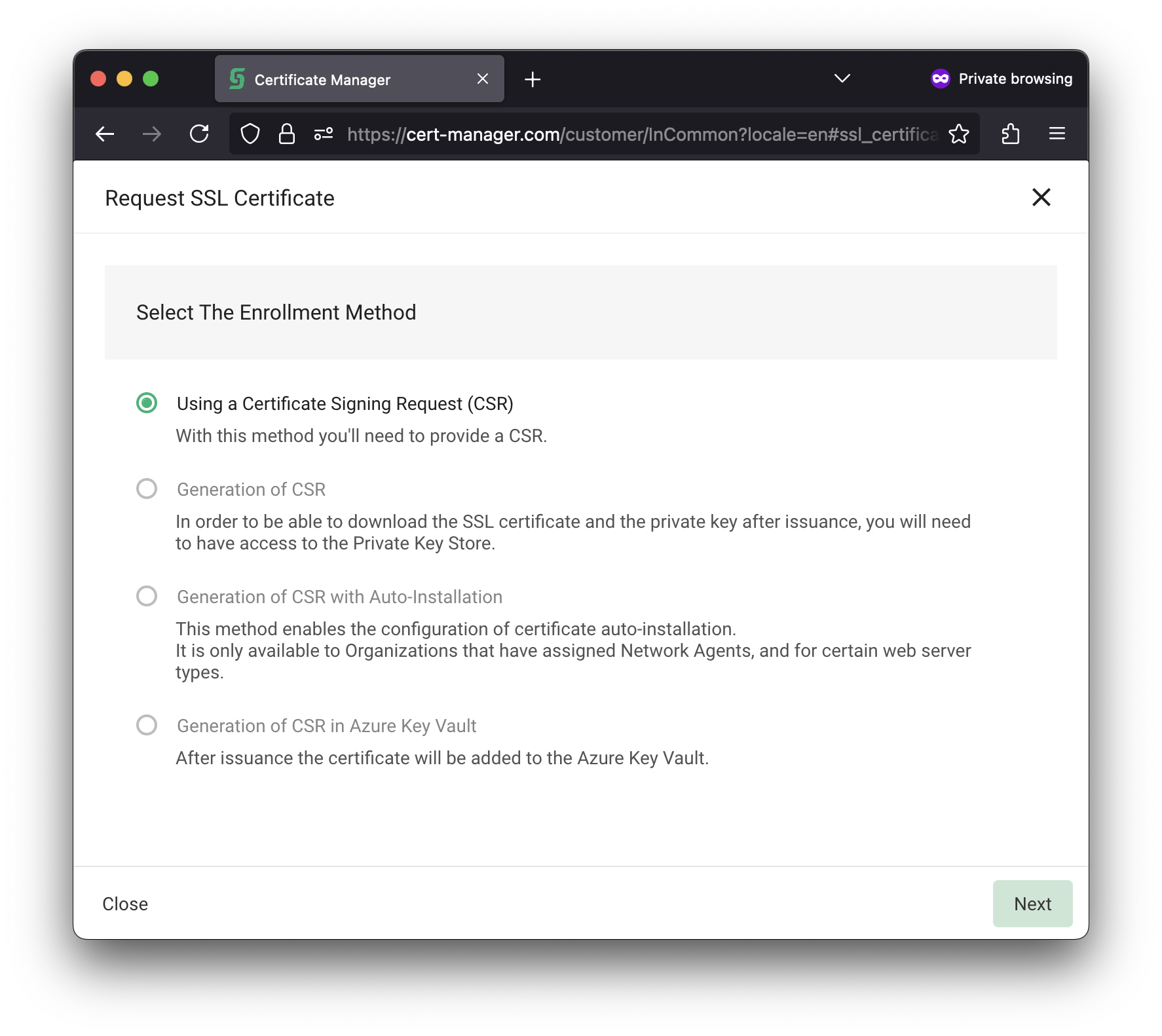 | Choose "Using a Certificate Signing Request (CSR)" and click Next. |
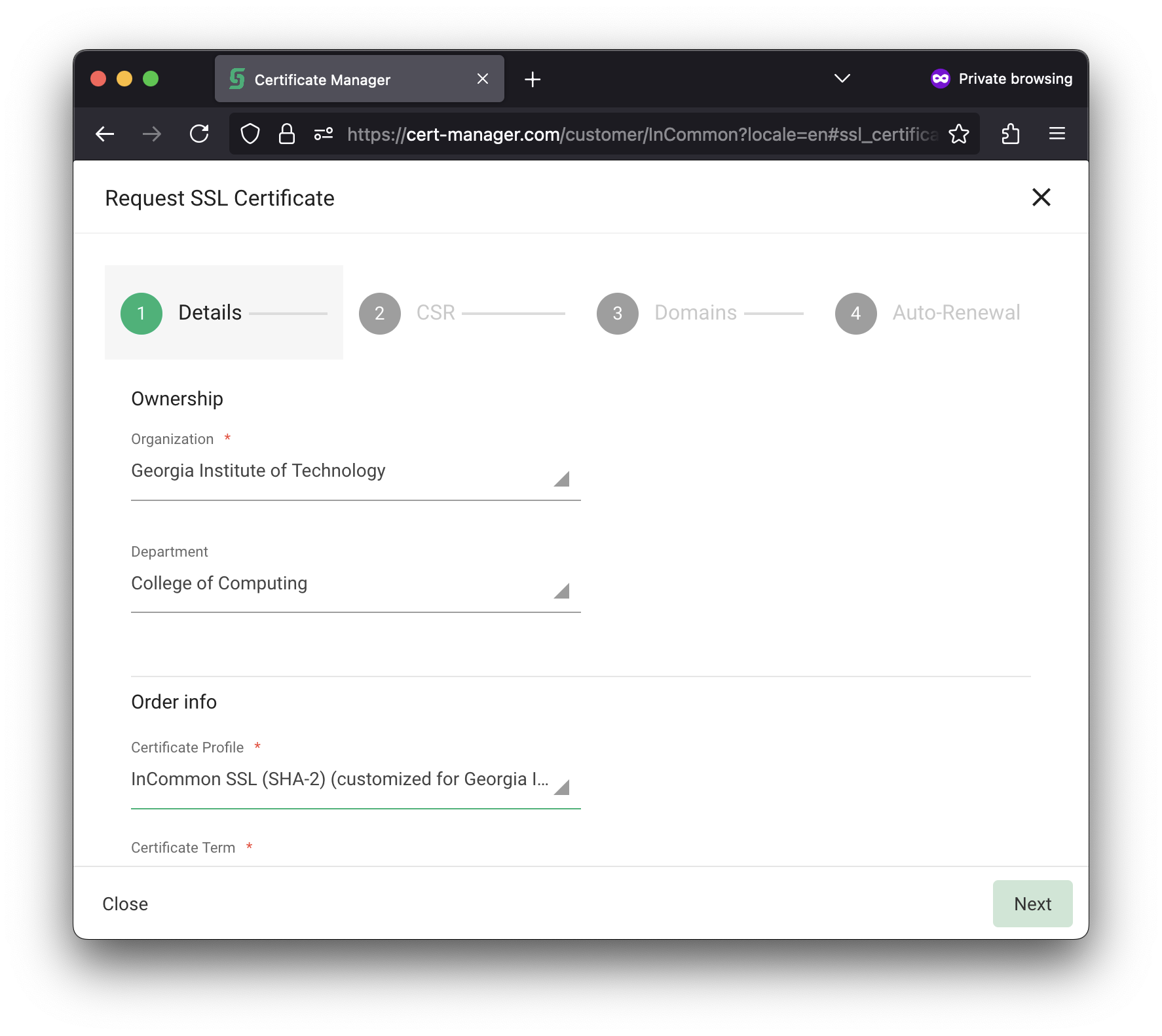 | For the Certificate Profile, choose either: For Notifications: |
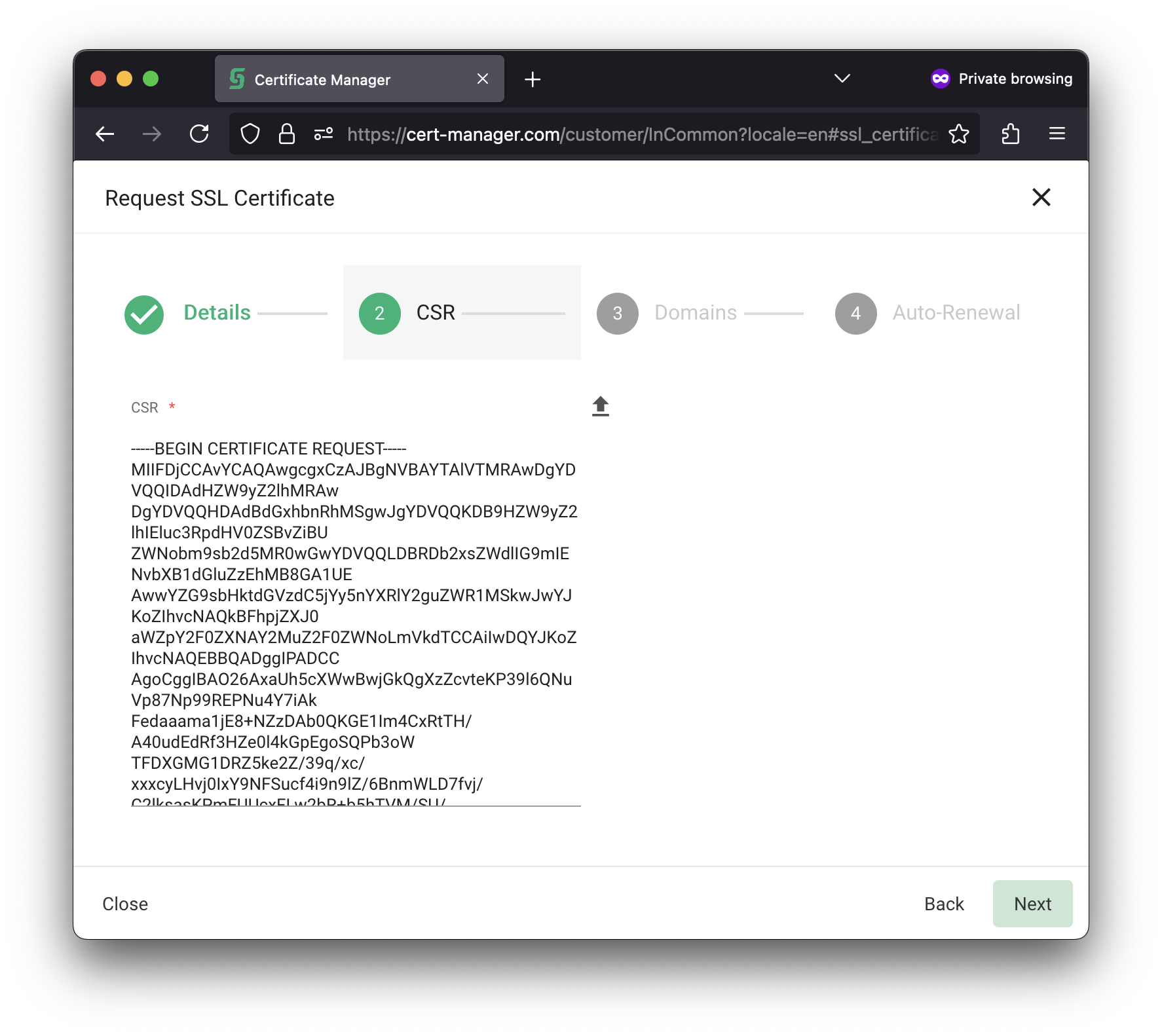 | Acquire the contents of the Certificate Signing Request (CSR):cat /etc/pki/tls/certs/<canonical-hostname>.cc.gatech.edu.csrPaste the contents of the Certificate Signing Request (CSR) into the box on step 2. |
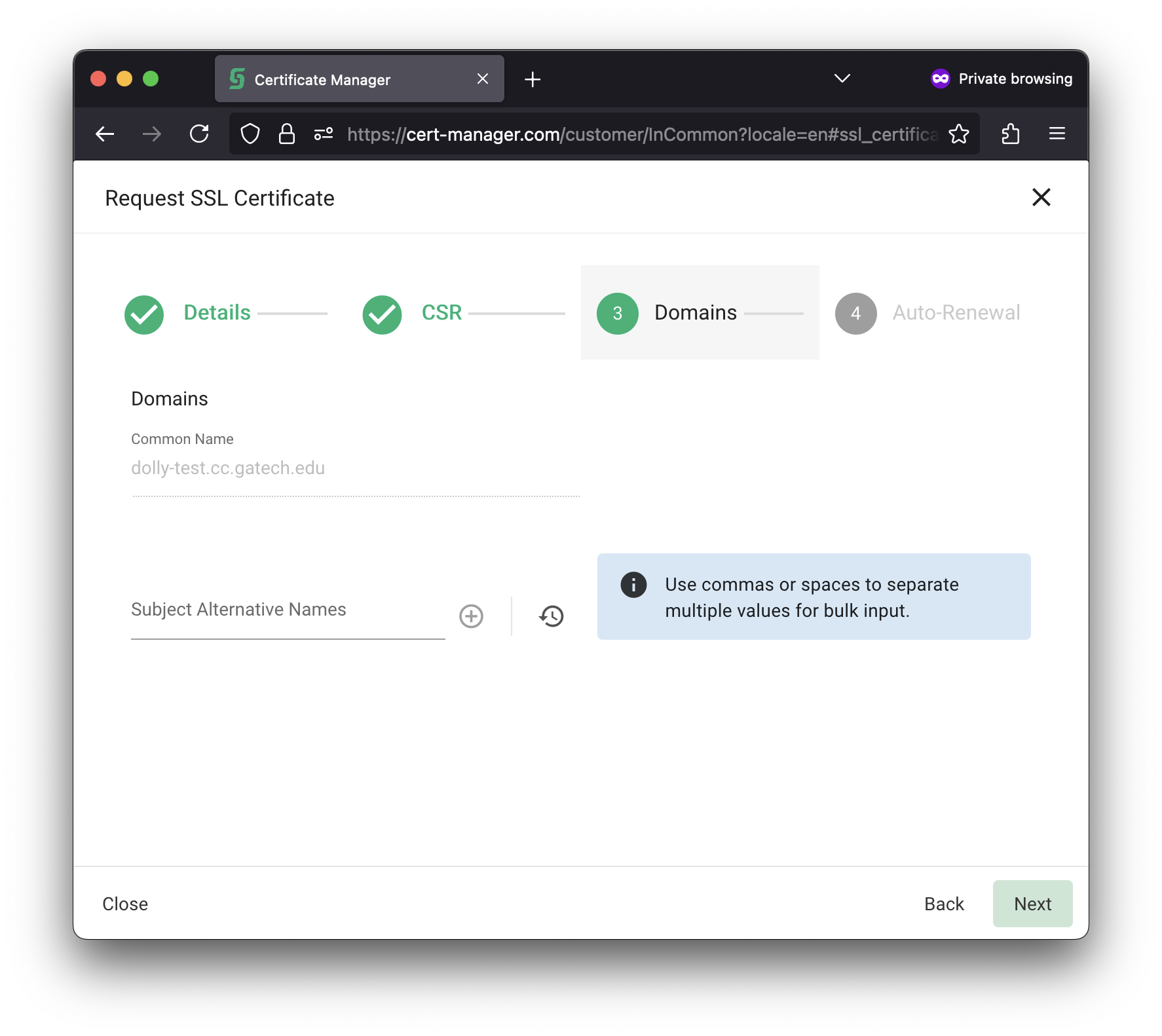 | Enter any additional hostnames into the Subject Alternative Names (SAN) field. This is for any additional domain names that are hosted on this server. For example, if you have app-test.cc.gatech.edu hosted on dolly-test.cc.gatech.edu, then app-test.cc.gatech.edu is the SAN. Note that this is per-server; you cannot put all the SAN domains for your project on the same certificate and use it across multiple servers. |
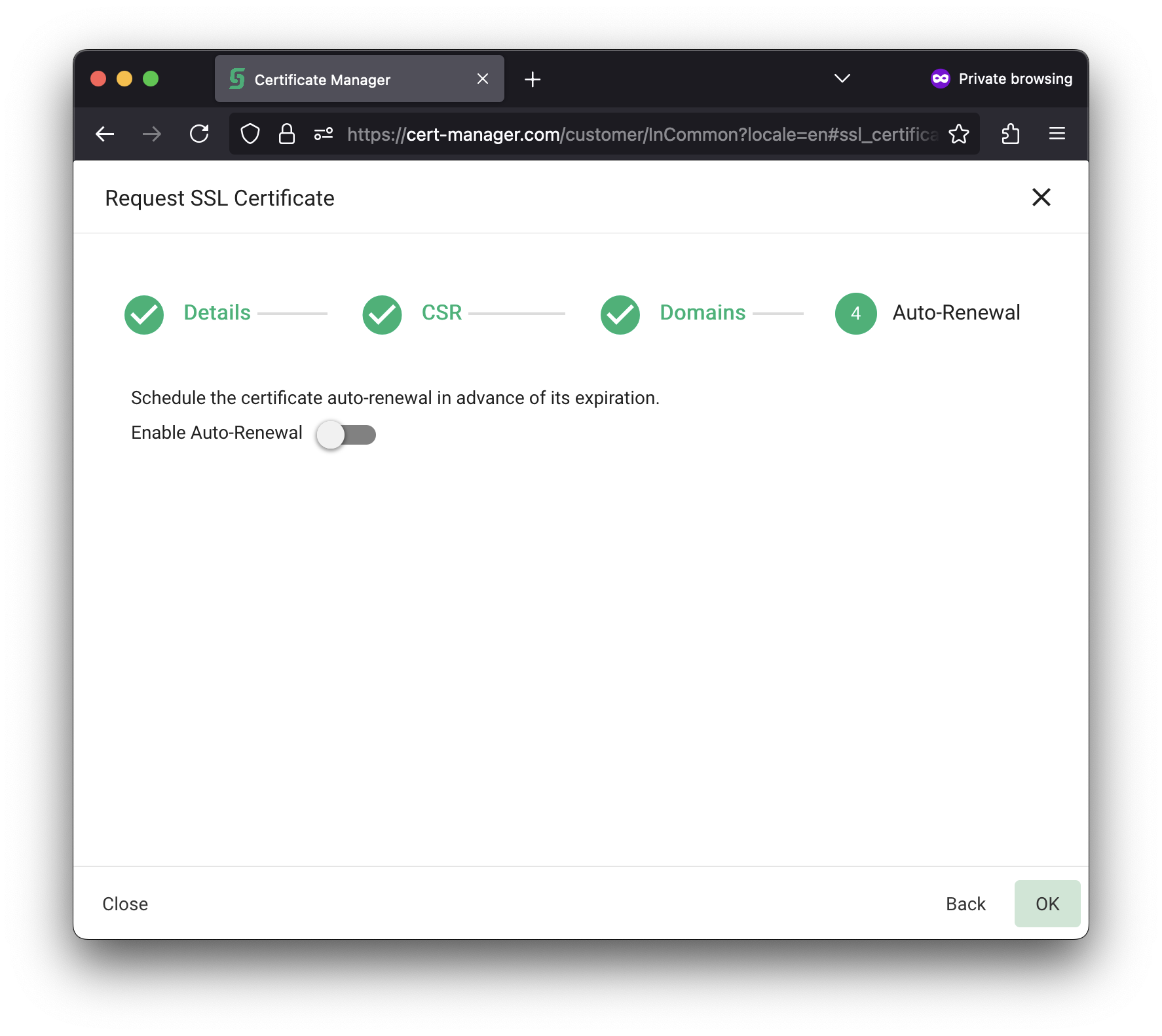 | On step 4, make sure that Enable Auto-Renewal is deselected. |
Acquiring Your Certificates
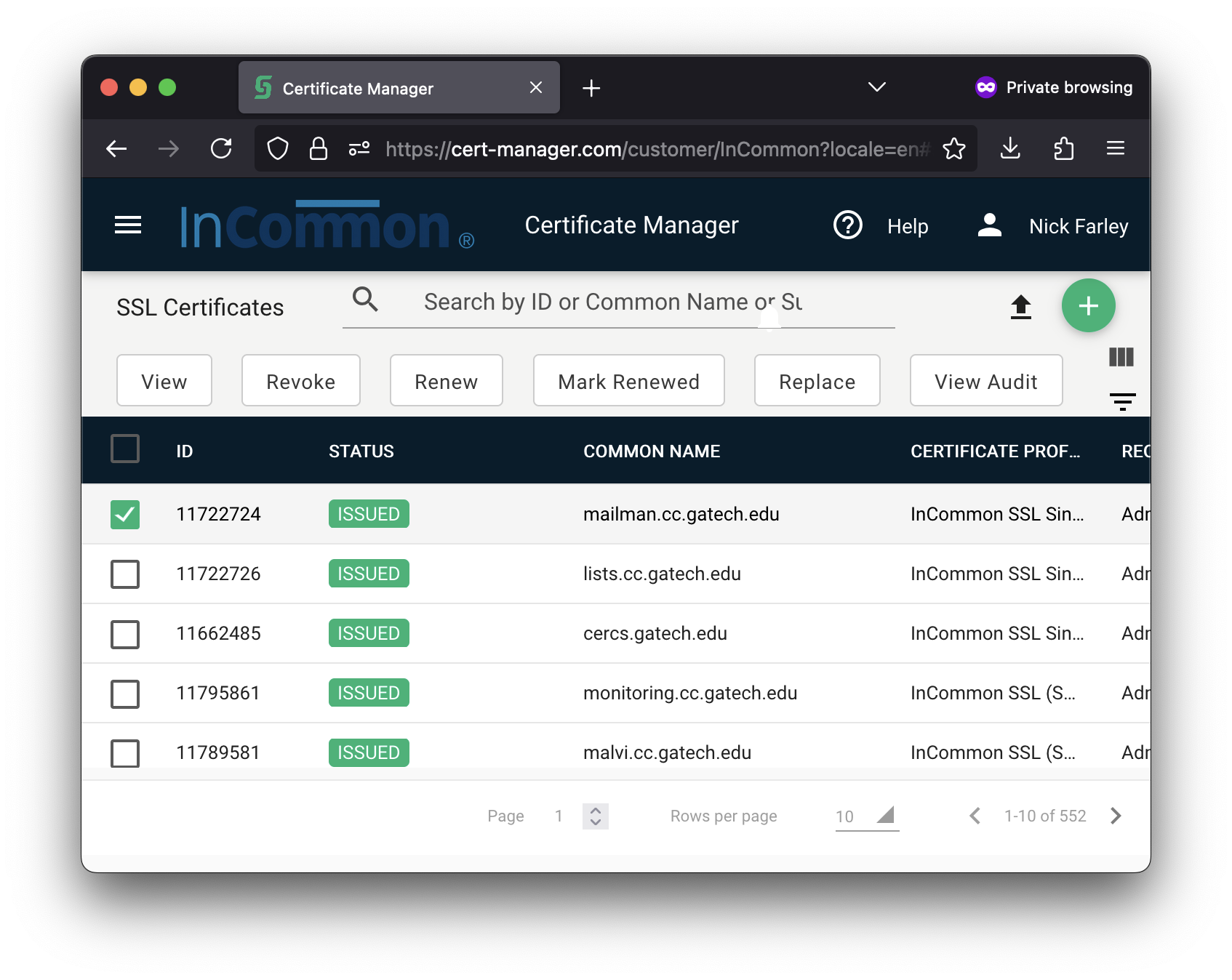 | Select the checkbox for the certificate you want to download, which should cause the toolbar above to appear. Click on the View button. |
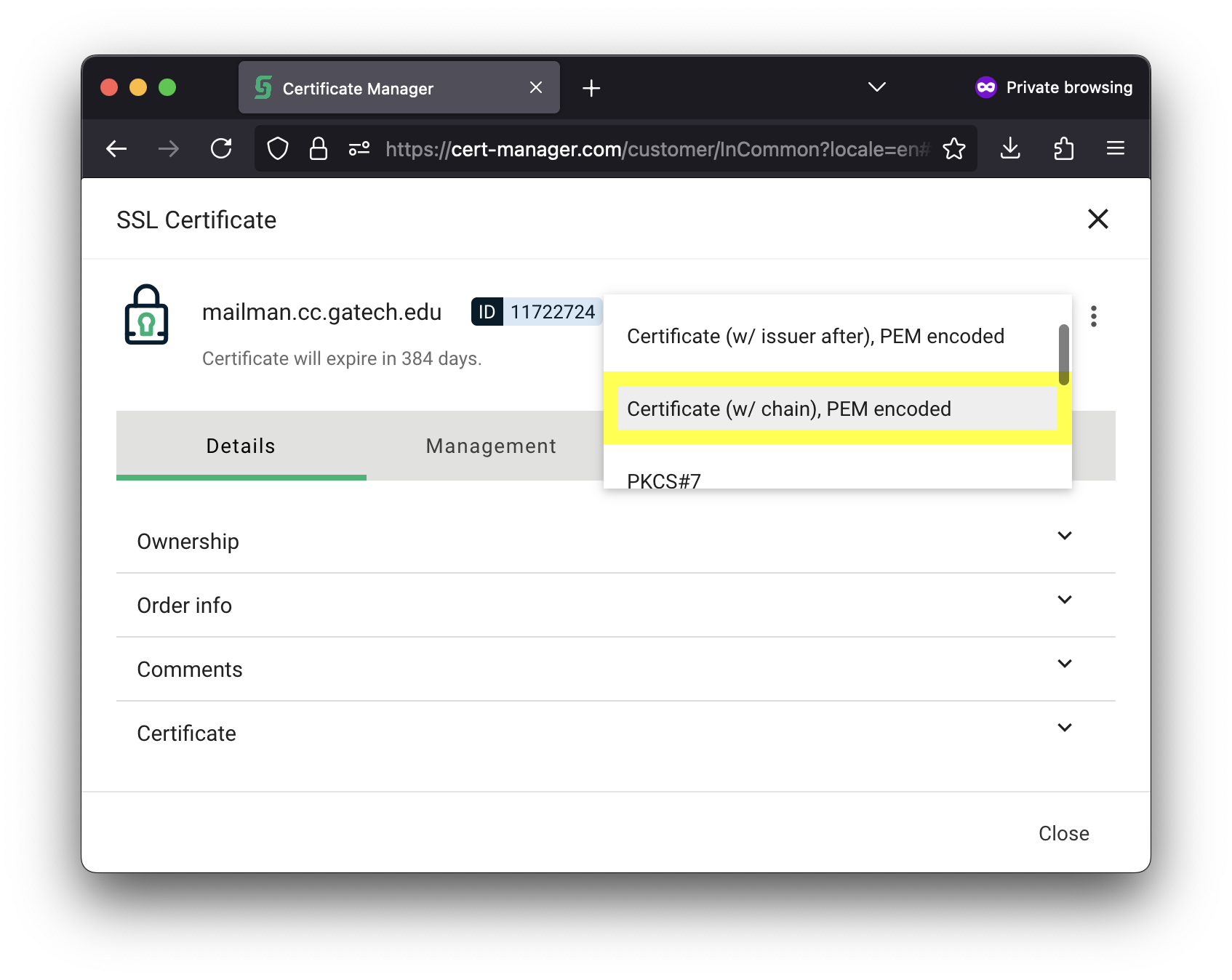 | On the certificate page, click on the grey Download Icon, and then select Certificate (w/ chain), PEM encoded (highlighted in yellow). This will download your certificates and all the intermediate certificates to establish a chain of trust. |
Install the Certificates on the Server
The downloaded file will contain four certificates, demarcated by -----BEGIN CERTIFICATE----- and -----END CERTIFICATE----- tags. The first three certificates make up the trust chain, while the fourth certificate is your actual certificate.
The final certificate should be created in /etc/pki/tls/certs/<canonical-hostname>.crt.
The chain of trust certificates should be placed in /etc/pki/tls/certs/<canonical-hostname>.chain.crt.
Using Ubuntu? Your certificate files should be in /etc/ssl/certs
Configure Apache to Use the New Certificate
The last step is to configure the web server to use the new certificate and certificate chain file. For apache on RHEL7, add/edit the following configuration directives to the appropriate VirtualHost definition in /etc/httpd/conf.d/<canonical-hostname>.conf. The actual name of the apache configuration file may vary.
SSLEngine on
SSLProtocol all -TLSv1.1 -TLSv1 -SSLv2 -SSLv3 SSLCipherSuite ALL:+HIGH:!ADH:!EXP:!SSLv2:!SSLv3:!MEDIUM:!LOW:!NULL:!aNULL SSLHonorCipherOrder on
SSLCertificateFile /etc/pki/tls/certs/<canonical-hostname>.cc.gatech.edu.crt SSLCertificateKeyFile /etc/pki/tls/private/<canonical-hostname>.cc.gatech.edu.key SSLCertificateChainFile /etc/pki/tls/certs/<canonical-hostname>.cc.gatech.edu.chain.crt
Restart apache (on RHEL 7): systemctl restart httpd
Certificate Renewal
To replace an expiring certificate, use the same CSR from the server in the process listed above. Once a renewal certificate is issued, you need to install the new cert (but don't have to change the original key or chain files). Use these steps:
- Copy the existing cert file to a .bak file.
- When InCommon approves the new cert, I copied its text contents and replaced those in the old cert file.
- Restart apache/httpd.
References
- SSL and TLS Deployment Best Practices (from SSL Labs)
- Test your SSL config with SSL Labs or use SSLTest.sh for servers that are behind the VPN
- http://en.wikipedia.org/wiki/Certificate_authority
- http://www.madboa.com/geek/openssl/
- http://www.openssl.org/docs/apps/openssl.html
- http://apetec.com/support/GenerateSAN-CSR.htm
- https://geekflare.com/san-ssl-certificate/
- https://www.namecheap.com/support/knowledgebase/article.aspx/10314/33/ssl-certificate-installation-on-apache2-debian-ubuntu/