Scope: All faculty, staff, students, and others using the College of Computing information technology resources.
Definitions:
- OIT: Office of Information Technology
- USG: University System of Georgia
- TSO: Technology Services Organization
- SSP: The System Security Plan (SSP) has been developed and will be used to protect all systems storing and processing CUI thus requiring compliance with the Defense Federal Acquisition Regulation Supplement (DFARS) clause 252.204.7012 Safe Guarding Defense Information and Cyber Incident Reporting.
- FRE SSP The Fundamental Research Exemption Standard System Security Plan (FRE SSP) has been developed and will be used to protect all systems storing and processing non-CUI data under the Defense Federal Acquisition Regulation Supplement (DFARS) clause 252.204.7012 Safe Guarding Defense Information and Cyber Incident Reporting.
- TCP: Technology Control Plan: The purpose of a TCP is to control the dissemination of controlled information, data, or defense service as defined in the export regulations to non-US persons. A TCP may also be used to control dissemination of research results as required by any research agreement.
SSP including the FRE SSP
The SSP is normally generated by a collaboration with GRC, OSP, and the Researcher who was awarded a DFARS or another project requiring one. GA Tech uses DFARS as it is the most common and would cover most controls required by any other project control needs.
TSO is contacted to ensure the controls are possible and can be maintained and may be contacted to assist in documenting the technical controls.
TSO can only be responsible for controls on TSO-controlled networks and TSO-managed endpoints and must be aware the SSP exists.
SSP Locations
All SSPs for COC are stored in a SharePoint vault controlled by GRC. Here, COC-Projects and read access can be requested. Although TSO has a copy at https://dropbox.com/home/CoC-TSO/Team%20-%20Infrastructure/CyberSecurity/SSPs , the GRC is the source of truth, which means the TSO location is only as good as the last time it was copied.
TCP
Not every SSP will require a TCP, but every TCP does require an SSP. A TSO representative signs off to ensure technical controls can be maintained. This information is provided in SSP. The need for a TCP is determined by OSP and GRC. TSO may be asked to consult on the technical controls.
TCP Locations
OSP maintains a copy of these which TSO has no access to other than asking for a copy. TSO does have to sign off and will get a finalized copy. These should be stored here
SSP/TCP Notification Areas
SSP and TCPs should be as readily accessible as possible to ensure TSO performs its due care and diligence to maintain the technical controls necessary within these forms. The following are the current locations to Identify if an SSP exits:
- DFARs SharePoint site: SSPs main repository. TSO does not get write access but can get ‘read’ access and alerts by requestion from GRC or from the site “request access” button.
- TSO Dropbox: coc-TSO/Team-Infrastructure/Cybersecurity/SSP or Technology Control Plan. These are copies of the DFARS SharePoint and emails for TCPS so TSO can track and ensure they are audited and current.
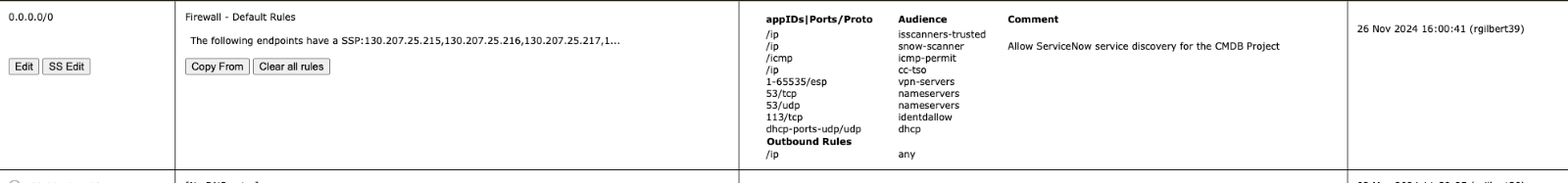
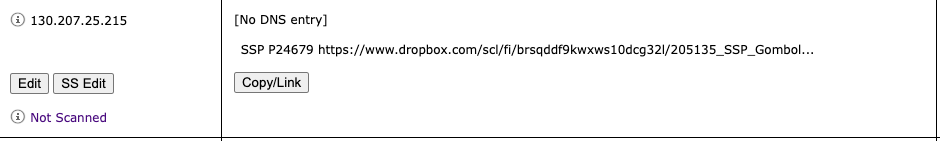
- Fw.noc.edu: Default Rules Should have IP addresses in its subnets with SSP listed Under name. This is performed by Selecting “SS Edit,” going to the “Server Attributes” box, typing in the “Server Comments” box, and selecting “Save Attributes.” Each IP with an SSP should have the SSP number and Dropbox URL is server comments. The entire URL will not show in the Name box, but clicking the “SS EDIT” button will allow for going to server comments so the URL can be copied and pasted for the SSP.
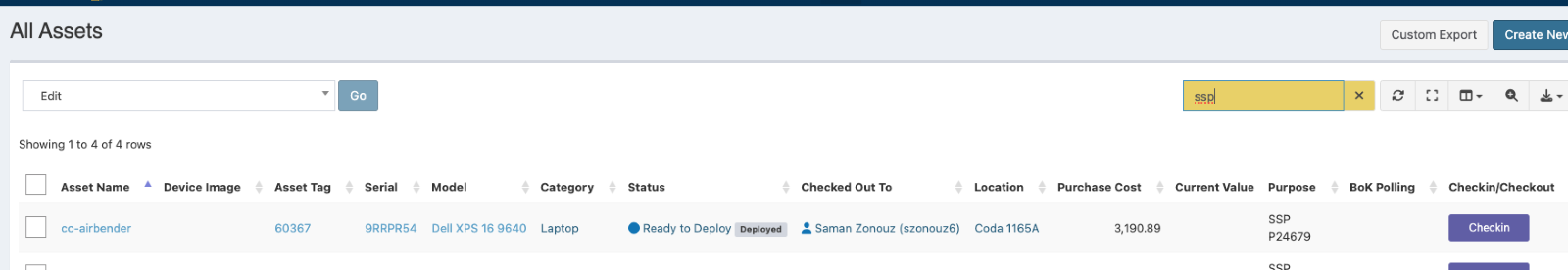
- Inventory.cc.gatech.edu: This is our Snipe-IT database. The Purpose field will contain the letters SSP and the SSP number. This will allow it to be searchable. TCP and number should also be entered if a TCP exists. The URL links to these forms will be added to “Notes” to allow for ease of navigation
- BOK: if DVLAN is set up for SSP or TCP endpoints, it will be in the comments to ensure people in BOK are aware and the endpoint is not moved from its location.
TSO Responsibilities:
TSO is responsible for maintaining the technical controls for the system security plan. Any issues should be reported to the PI or the person designated by the PI to resolve issues. TSO should ensure issues are resolved per SSP and GT standards. If any issue is not or cannot be resolved, it should be brought to the attention of TSO leadership and coordinated with PI as GRC and Cybersecurity will need to be notified for the next steps. Issues can include but are not limited to items such as Opened ports on the Firewall, Vulnerabilities, and Security events (if not coming from OIT, they must be reported to OIT), Removal of Tools, unapproved software, And Security incidents, which must follow the security incident process.
TSO will review yearly to ensure SSPs and TCPs are still valid or needed and update locations as needed. FRE SSPs are good for 1 year so if needed, the PI will need to resubmit a new one.
Links to More Information
- USG Information Technology Handbook: https://www.usg.edu/information_technology_services/it_handbook/
- GT Cybersecurity site: https://security.gatech.edu/
- GT Cybersecurity Policy: https://policylibrary.gatech.edu/information-technology/cyber-security-policy
- GT Incident Response Procedure: https://security.gatech.edu/incident-response/
- TSO helpdesk: https://support.cc.gatech.edu/
- System Security Plan documentation: https://cui.gatech.edu/gt-standard-system-security-plan/
- Technology Control Plan documentation: https://generalcounsel.gatech.edu/ethics-and-compliance/exportandtrade/TCP